Max: BloodHound Domain Password Audit Tool
TLDR
Github: github.com/knavesec/Max
The introduction of the Domain Password Audit Tool (DPAT) a few years ago was a great way to have a graphical display of password cracking audits (github.com/clr2of8/DPAT). The capability to export domain groups to check which members had been cracked was great, but since we already ingested domain group information with BloodHound, it would be far more valuable to just map those users to the database information.
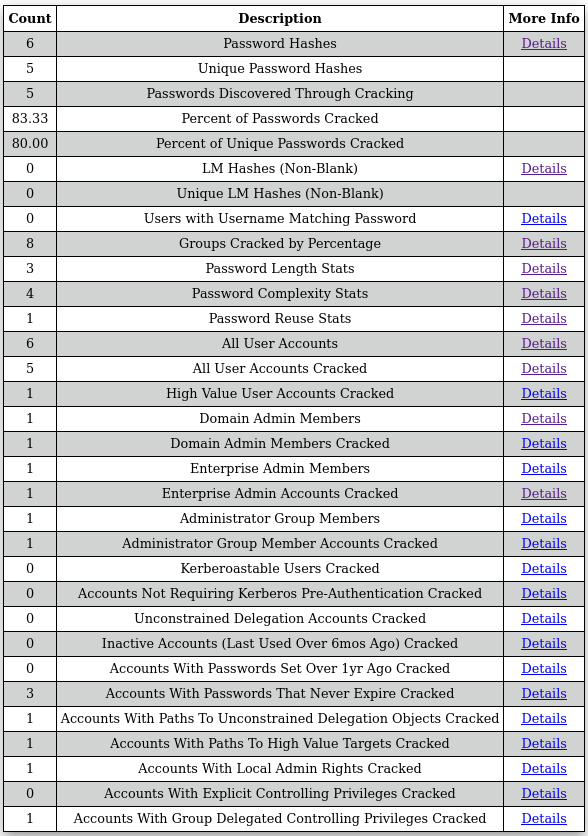
The goal of the DPAT module was to combine the information and pathfinding of BloodHound with password analytics, all outputable to HTML, ASCII art and CSV formats. This module searches for:
- All the stats that come with the original DPAT tool
- Accounts with passwords that never expire cracked
- Kerberoastable users cracked
- High value domain group members cracked
- Accounts with paths to unconstrained delegation objects cracked
- and much much more…
Shoutout to @blurbdust, the DPAT module was his idea and we worked together for quite a while to put it together. This release also includes a full port to python Windows functionality.
Full Post
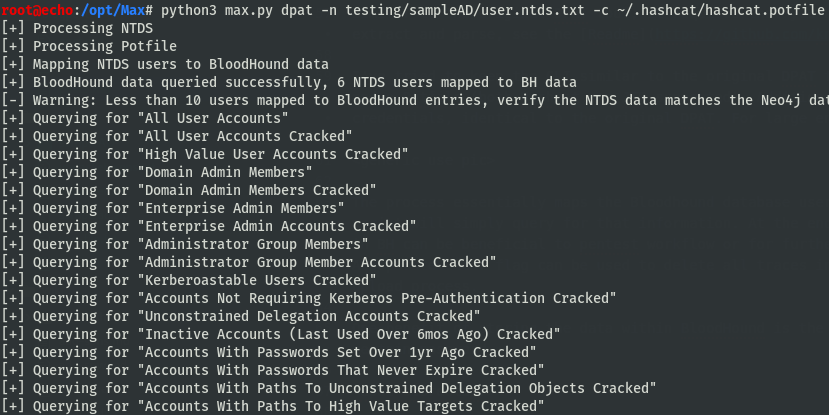
While using the original DPAT tool, the thought was “Why do I need to extract domain groups again, I already have all the information within BloodHound?”. It took a bit of work to figure out how to correlate NTDS users to BloodHound since they’re in different formats, but at the end of the day it was possible by matching the RID & usernames to the BH data. This made it easy to not only look into group members cracked, but utilize the wealth of information already ingested by BloodHound to find more trends and significant patterns.
So far, this DPAT module looks for:
- Cracked password percentages
- Password length, reuse & complexity stats
- Specific high-value group members cracked
- Group specific crack rates
- Kerberoastable & AS-REP roastable users cracked
- Inactive accounts cracked
- Accounts with passwords set to never expire & with passwords set over 1yr ago cracked
- Accounts with paths to HVTs & unconstrained delegation systems cracked
- Accounts with local administrator or other control privileges cracked
Then all affected users are filtered by whether or not they are enabled. I will note, this currently doesn’t include additions for the Azure & the AzureHound edges, it’s tailored for typical AD environments. PR’s welcome for Azure improvements.
General Usage
Similar to the original DPAT tool, it requires that you have an extracted NTDS.dit file that has been parsed with Impacket Suite’s secretsdump tool. I won’t go into detail on how to extract and parse, see the Readme file for that.
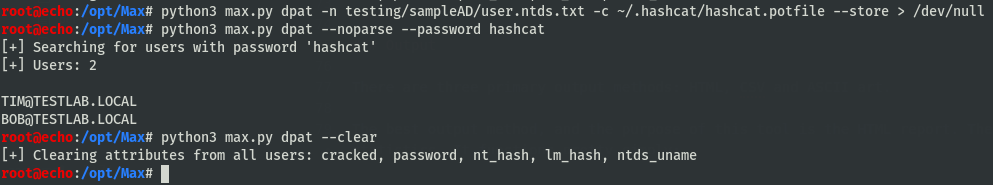
I’ve tried to keep the CLI similar to the original DPAT tool, so at the end of the day it would feel familiar. I took the time to port everything to Windows as well, to allow any Windows based sysadmins the same pleasure. The only two necessary inputs are an NTDS file (parsed by secretsdump) and a Potfile (both Hashcat and JTR supported). Additionally, since this handles all passwords & hashes for an organization, we’ve provided a “sanitize” option to obfuscate credentials, identical to the original DPAT. For large environments, there is an option to increase the thread count for the upload process.
The process maps the Bloodhound database users to the NTDS users, then uploads their NT/LM hashes and passwords into the database. When performing password analytics, the script will simply query for that information. At the end, all data uploaded will be sanitized from the database. Sometimes, however, keeping hashes and passwords tied to the AD users in BH can be beneficial to pentest workflow or for further analysis. A Store option has been added which will write all the information to the database but won’t clear it at the end. A separate Clear flag can be used to delete all traces independently. If data has already been uploaded, you can use the NoParse flag to do password analytics and skip the parsing/upload process.
One benefit of storing the data within BloodHound is the search functionality of uploaded passwords. You can search for the password of an input user, or match any user who has a certain password.
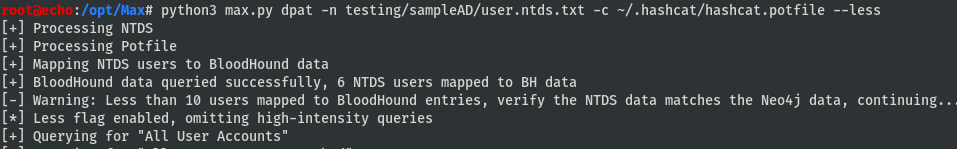
On some bigger AD environments, pathfinding queries can take excessively long times. A “less” flag has been included to remove time-intensive queries. This only omits the following queries:
- Group Statistics
- Accounts with paths to HVTs & Unconstrained delegation objects
- Accounts with Local Admin privs
- Accounts with other controlling privs
Output
There are three primary output methods: HTML, CSV and ASCII art.
The best output method, and the purpose of this tool is the HTML report. The design mirrors the original DPAT tool’s table output, simply with the addition of extra information and statistics. It functions pretty simply:
python3 max.py dpat <other args> --output outputdirectory --html

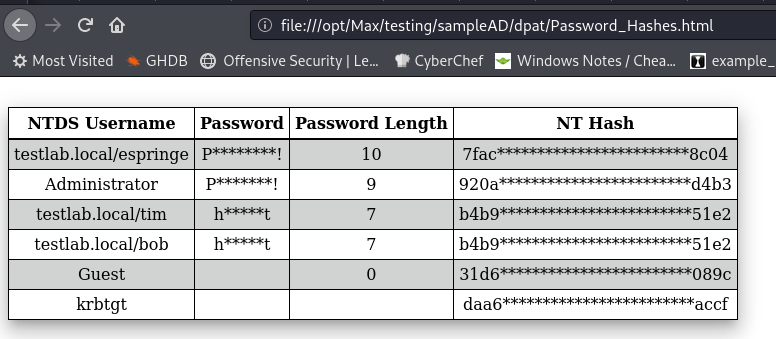
An additional method of output is more geared towards getting raw lists of users in the output in CSV format.
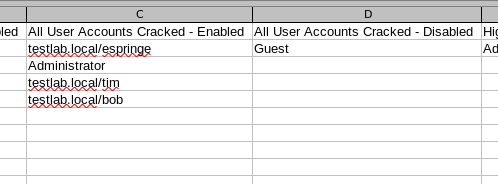
python3 max.py dpat <other args> --output outputfilename --csv
The last output method, omitting the -o/--output flag and output options will default to an ASCII art output. It’s splendid, courtesy of @blurbdust yet again.
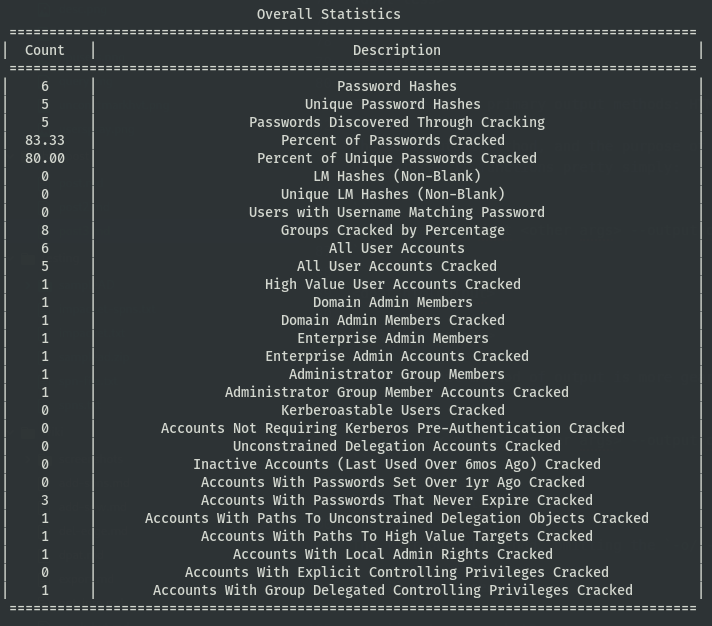
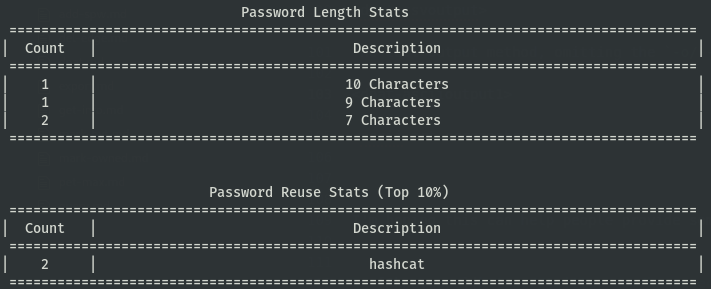
I’m hoping this can help people provide some insight into vulnerable users and groups within the environment, user passwords tend to be a weak link in the chain for many organizations. Always looking for improvements.